Share A Model-Driven App With An Entra Security Group

You can share a model-driven app, a security role and access to an environment all at once by adding a user to an Entra security group. This method of granting access makes it quick & easy to onboard a new user. And it also reduces the chance for errors during setup process. In this article I will show you my simple process for sharing model-driven apps.
Table of Contents
• Introduction: The Inspections App
• Create An Entra Security Group In The Azure Portal
• Locate The Security Role
• Setup A Dataverse Security Team Linked To The Entra Security Group
• Create A Nested Entra Security Group To Manage Environment Access
• Apply the Entra Security Group To The Power Platform Environment
• Share The Model-Driven App With A Security Role
• Test Access To The Model-Driven App
Introduction: The Inspections App
Inspectors who work at a large retail company visit stores to conduct an inspection. The inspection results are entered into the Field Inspections model-driven app.
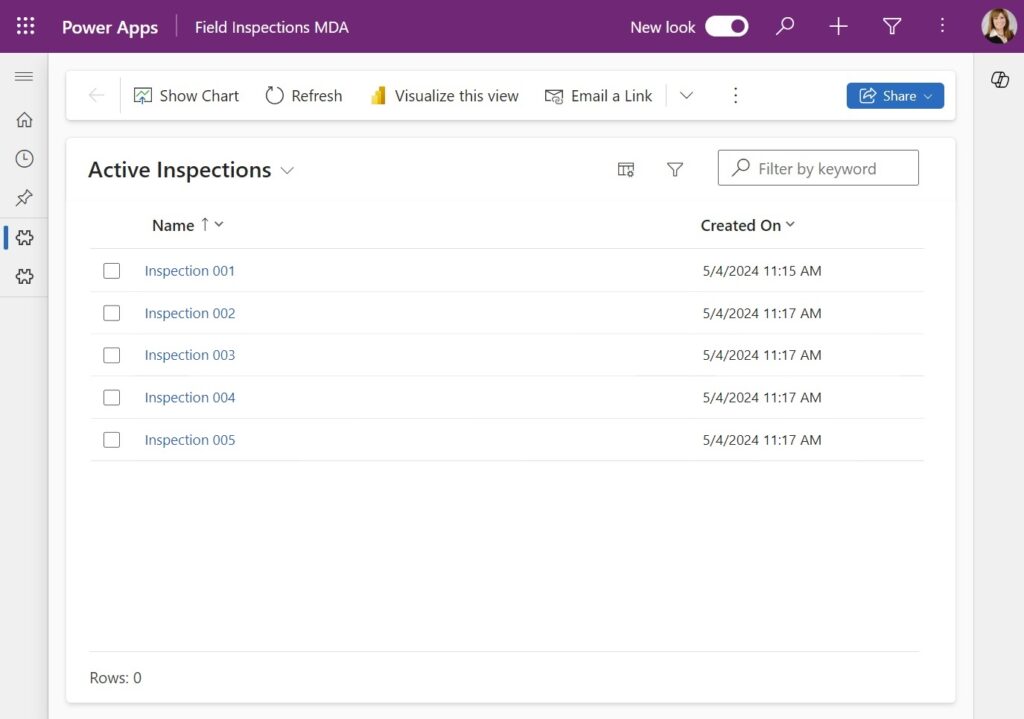
Access to the model-driven app, the environment and the appropriate security roles are granted through assigning an inspector to a single Entra security group.
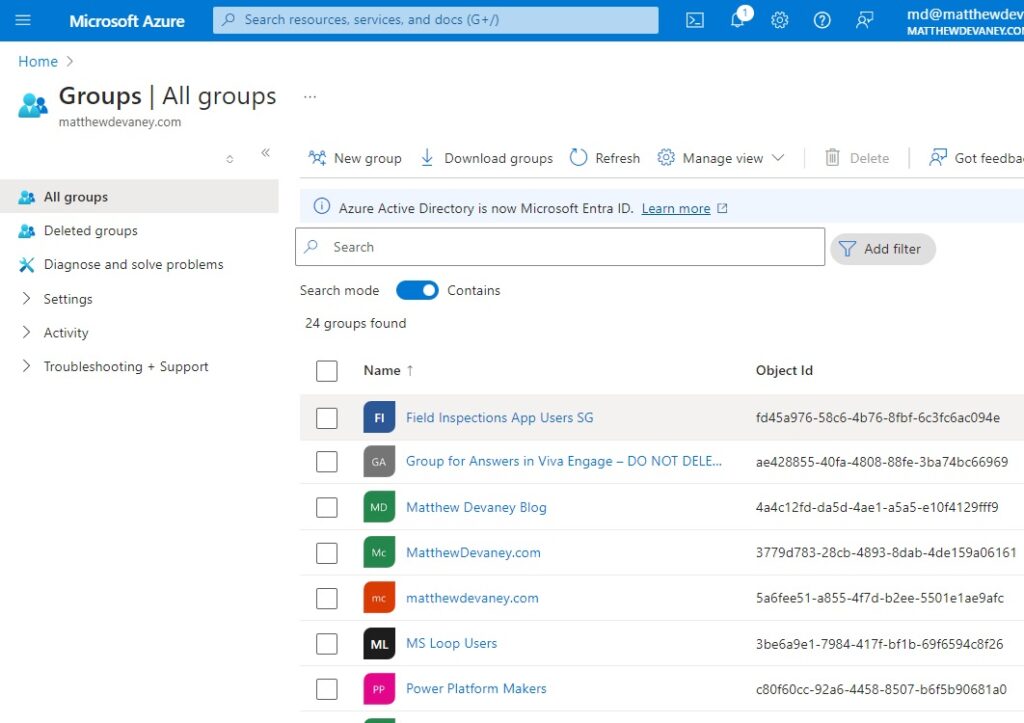
Create An Entra Security Group In The Azure Portal
When a user is added to the Entra security group they will be assigned a security role and be able to open the model-driven app. Open portal.azure.com and go to the Groups page.
Create a new group.
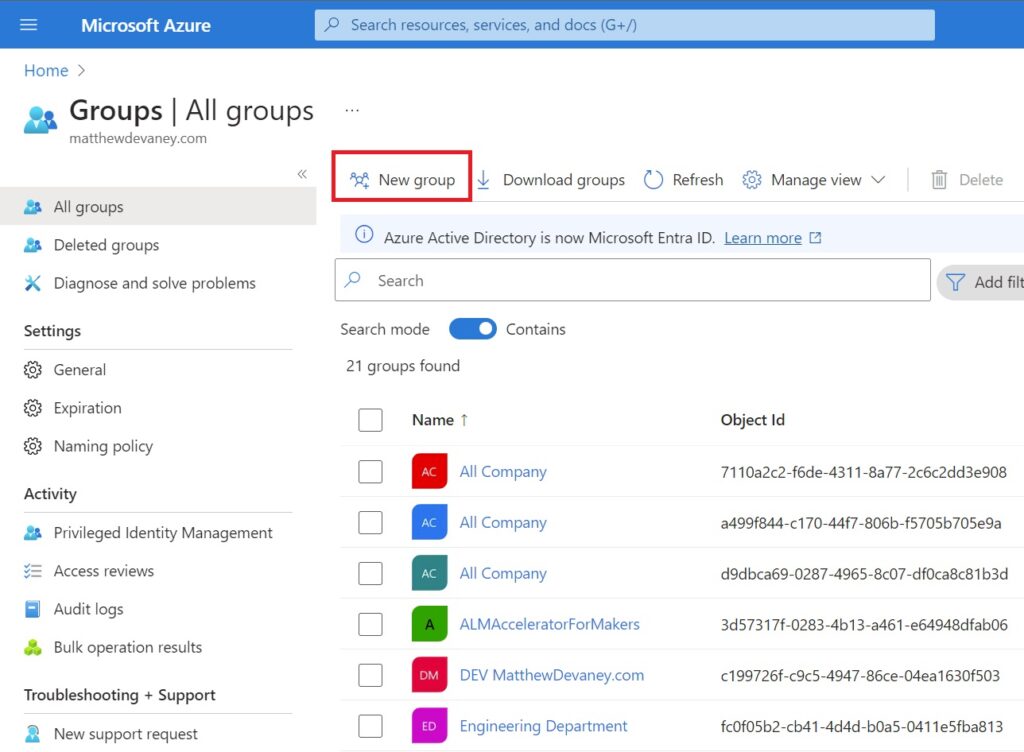
Choose the group type Security and name the group Field Inspections App Users SG.
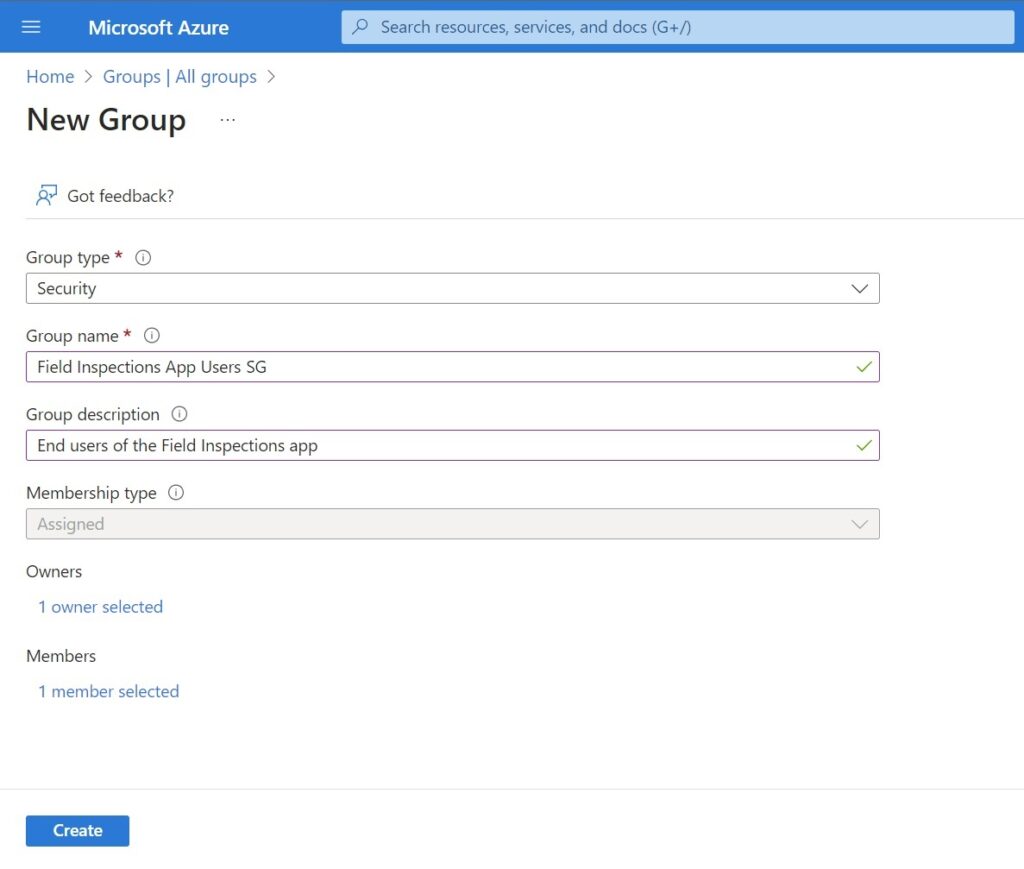
Assign any users who you want to have access to the model-driven app to the security group. The press the create button.
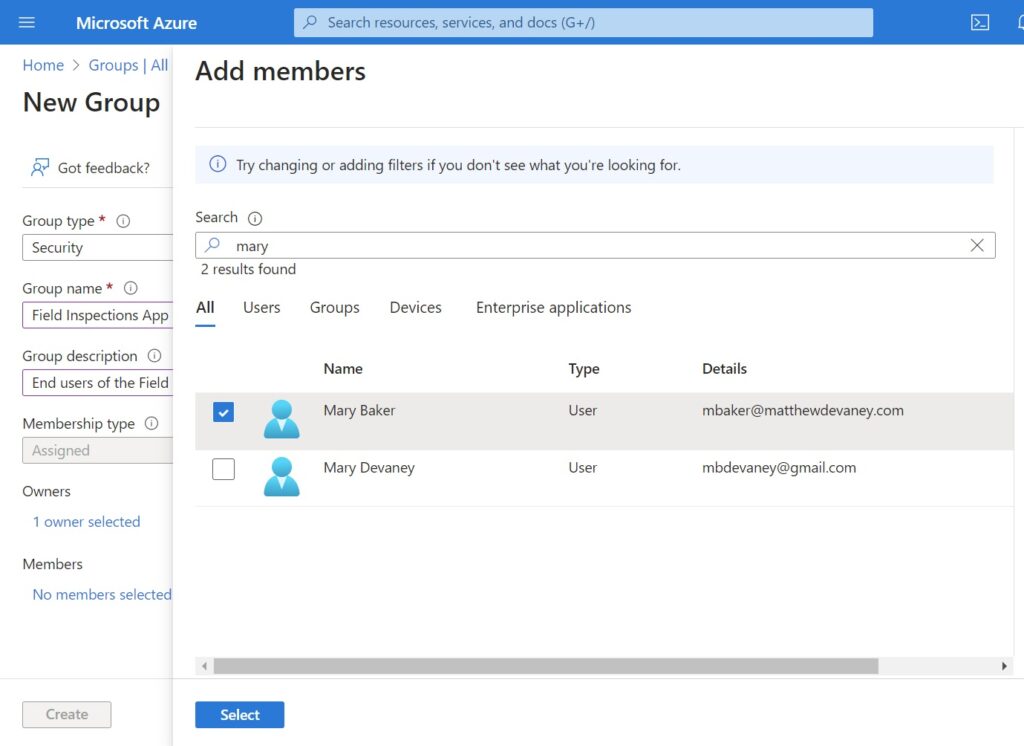
The Field Inspections App Users SG group now appears in the list of group.

Locate The Security Role
Model-driven apps sharing is governed by security roles along with access to tables. Before proceeding any further we will want to identify the security role that is granted when added a new user to the Entra security group. Open the Power Platform Admin Center, browse to the environment where the app is stored and then navigate to the Security Roles area.
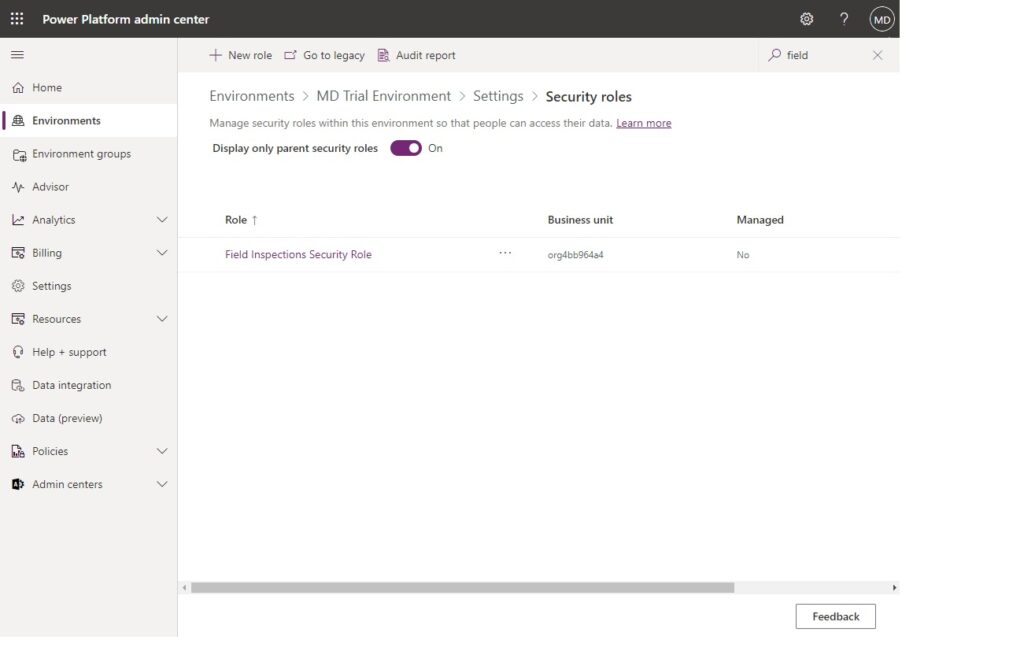
The security role should include any tables used by the model-driven app.
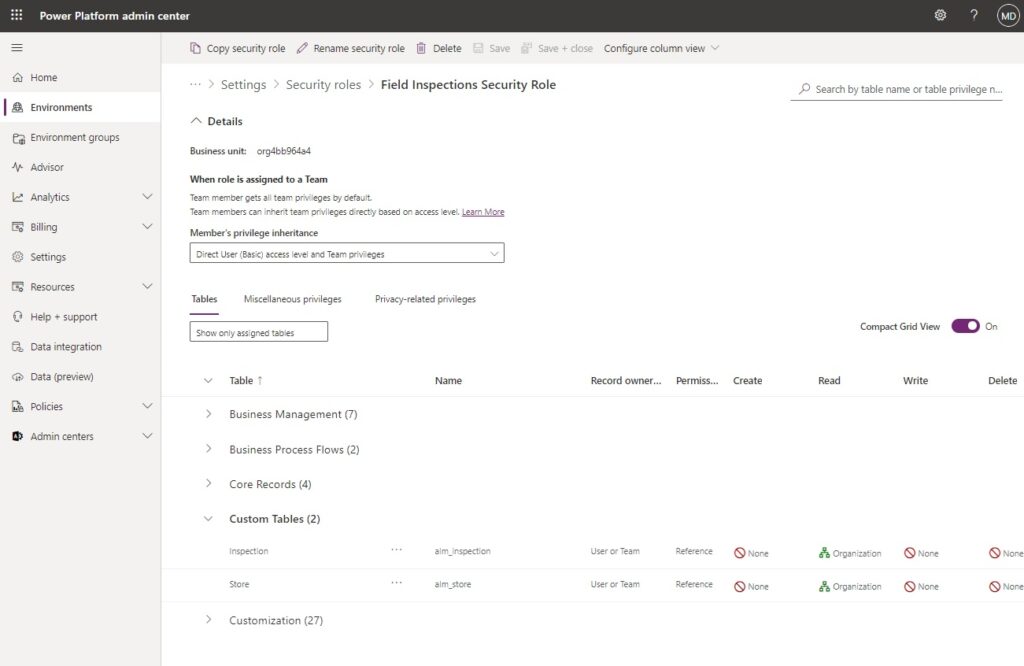
Setup A Dataverse Security Team Linked To The Entra Security Group
Model-driven apps cannot be directly shared with an Entra security group. App sharing is managed by security roles. We will need to setup a security team whose membership is governed by the Entra security group we created and grants the user the Field Inspectors security role.
Open the environment’s landing page in Power Platform Admin Center and go to the Teams page.
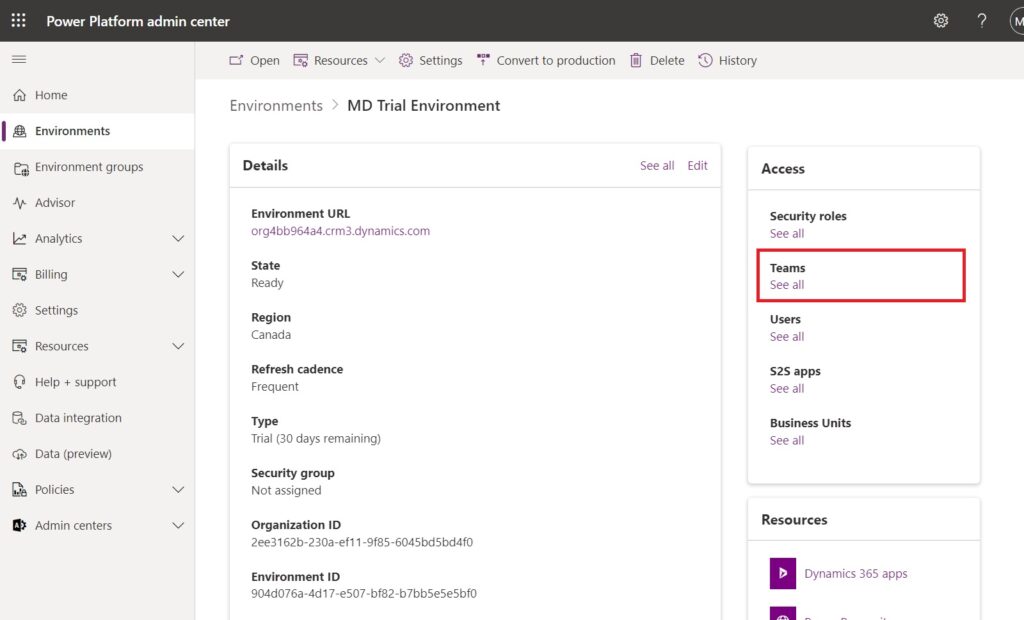
Create a new team.
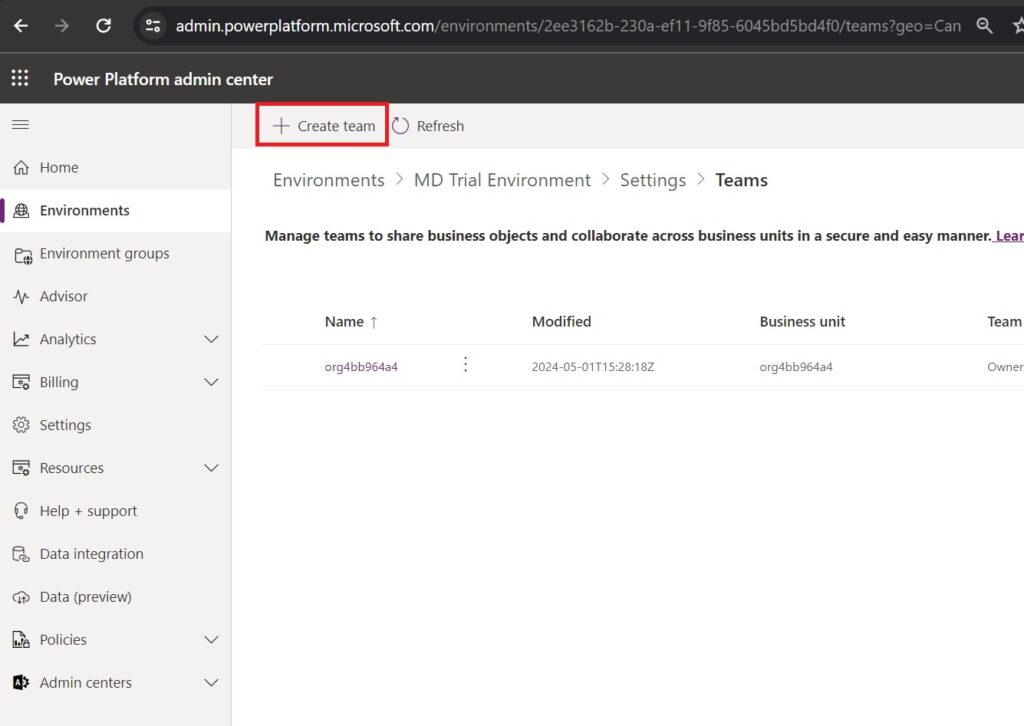
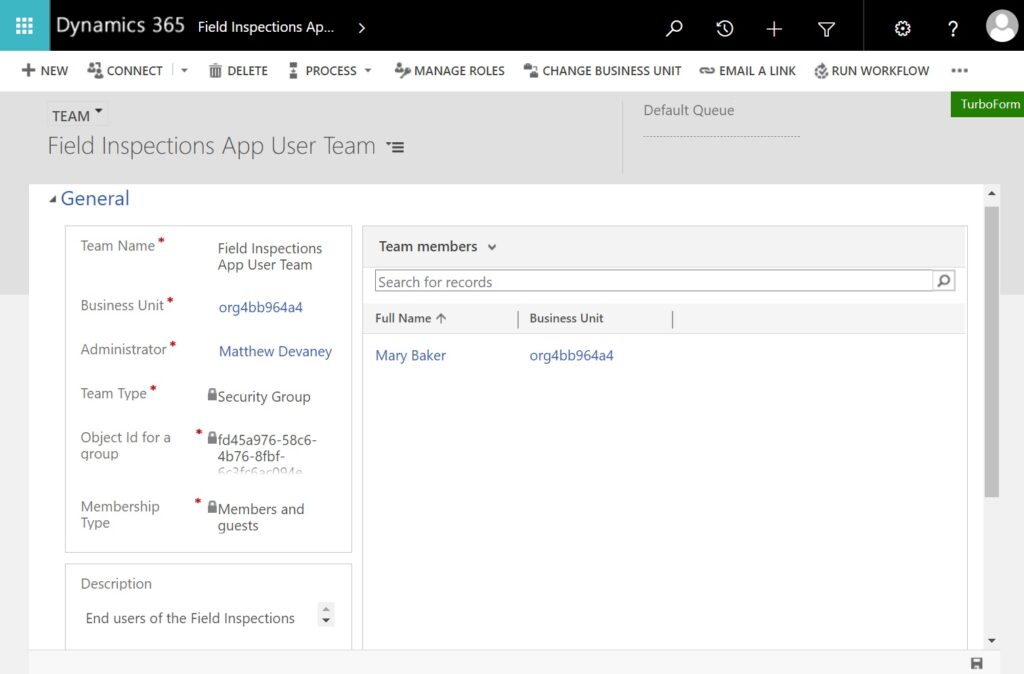
Setup the team per the following instructions and then press the next button:
- Team Name – Field Inspections App User Team
- Business Unit – default business unit for the environment
- Administrator – your name
- Team Type – Microsoft Entra ID Security Group
- Group Name – Field Inspections App Users SG
- Membership type – Members and guests
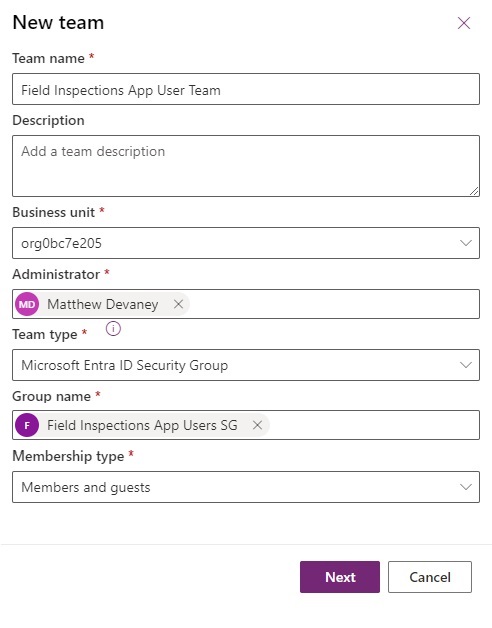
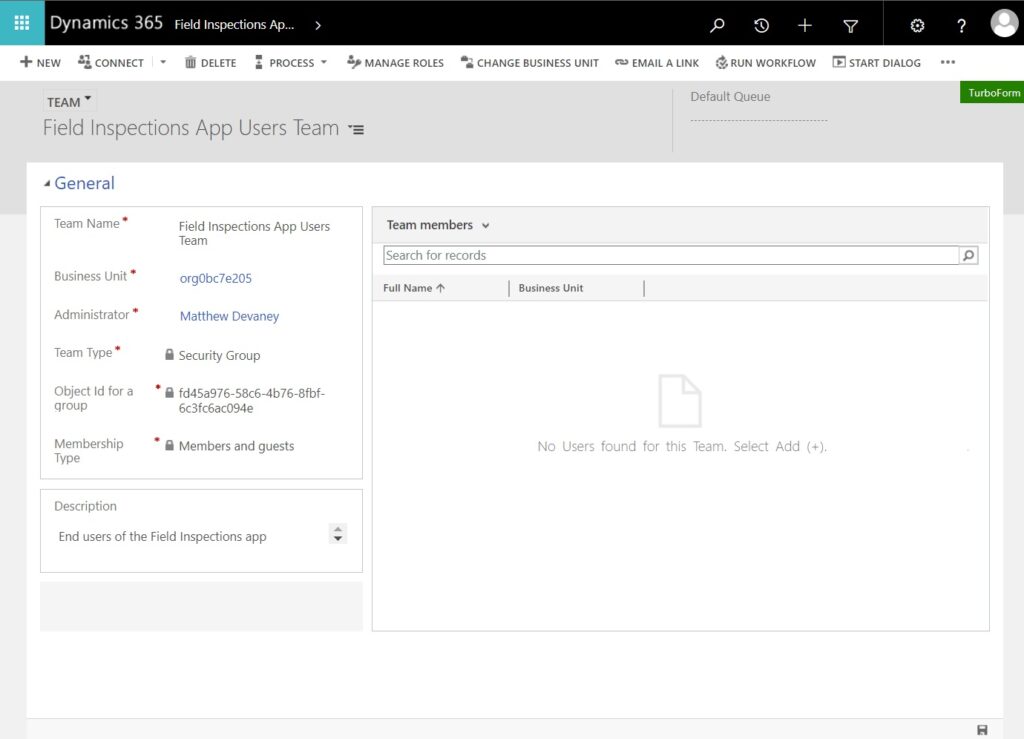
Select the Field Inspections Security Role. Then press the Save button.
The security team management page will appear. There are no users found even though we previously added them to the Entra security group. This is normal. Users will not appear in the security team or the environment until the first time they open the app.
Create A Nested Entra Security Group To Manage Environment Access
We also want to grant access to the environment where the app is located when we add users to the Field Inspections App Users security group. However, there are reasons we might not want to use that same group to control environment access. Perhaps there are multiple apps in the same environment that not all users should have access to. Or multiple security roles for a single app.
The solution is to create a nested Entra Security Group. We will make a new security group to govern environment access and then add the Field Inspections App Users security group to it as a member. This leaves open the possibility to add more security groups granting different levels of access in the future.
Go to portal.azure.com and create a new group.
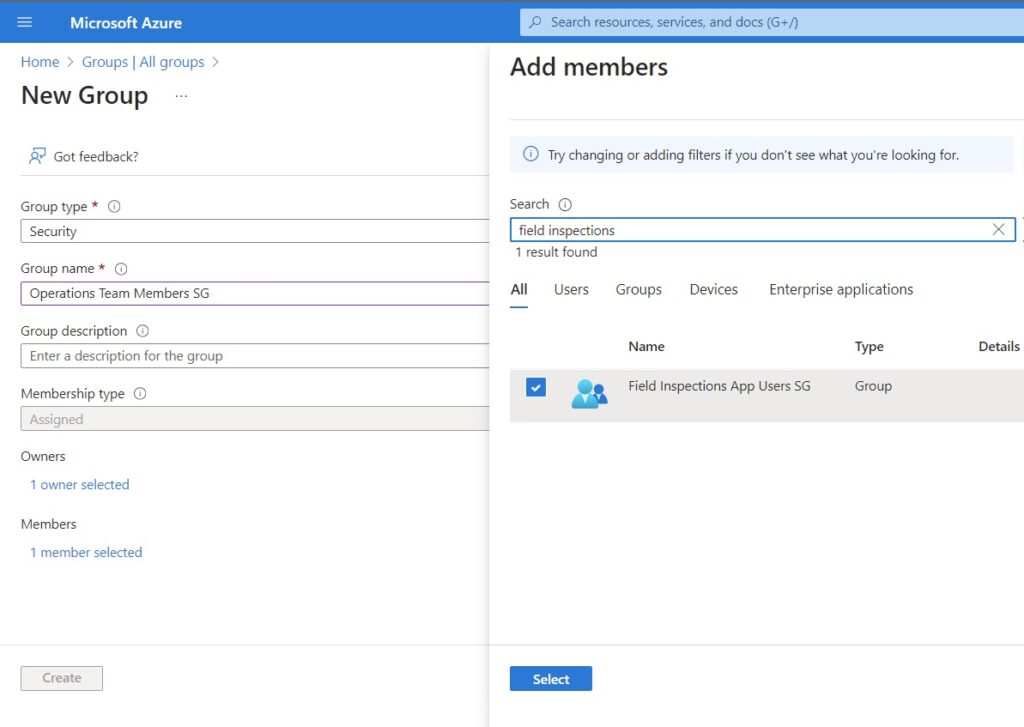
Use the group name Operations Team Members SG and add the Field Inspections App Users security group as a member. Then press the Create button.
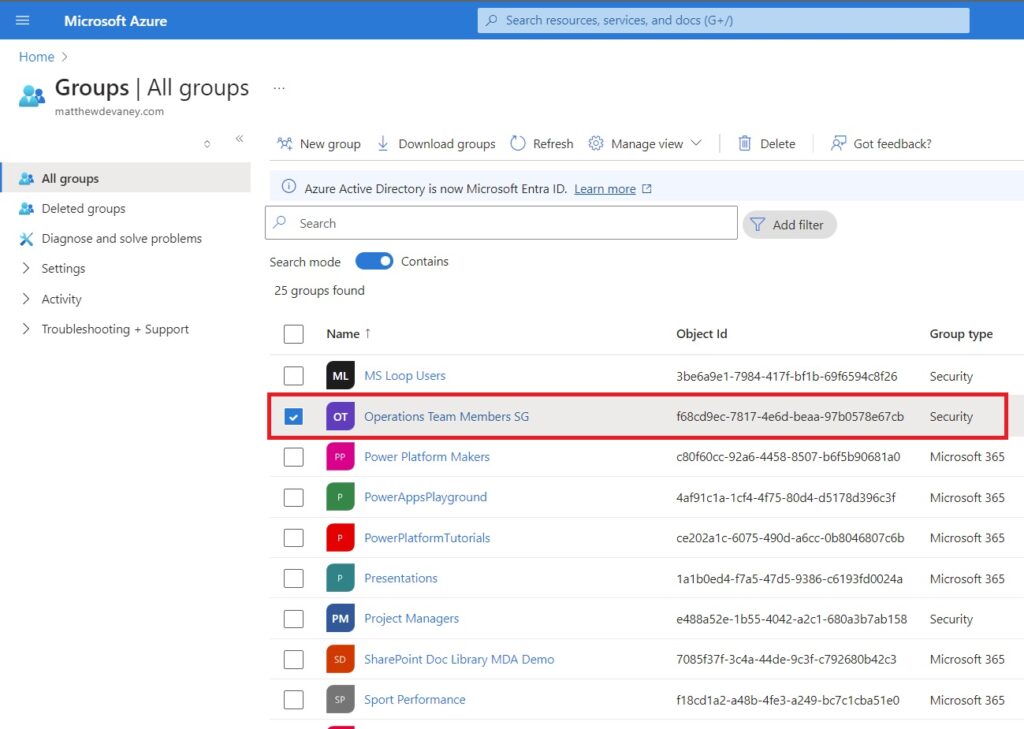
The Operations Team Members SG Entra Security Group appears in the groups list .
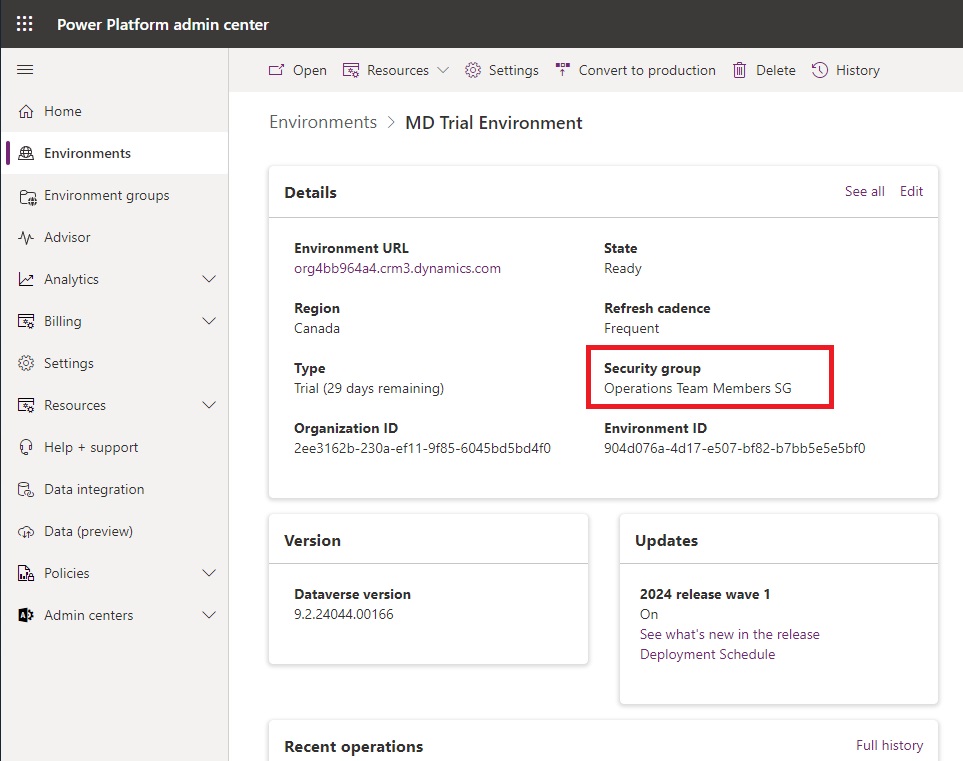
Apply the Entra Security Group To The Power Platform Environment
Go the the environment’s landing page in the Power Platform Admin center and select Edit on the Details group. Apply the Operations Team Members security group and press Save. Now only members of the security group may access the environment. They will not be added to the environment until the first time the user opens the model-driven app.
Share The Model-Driven App With A Security Role
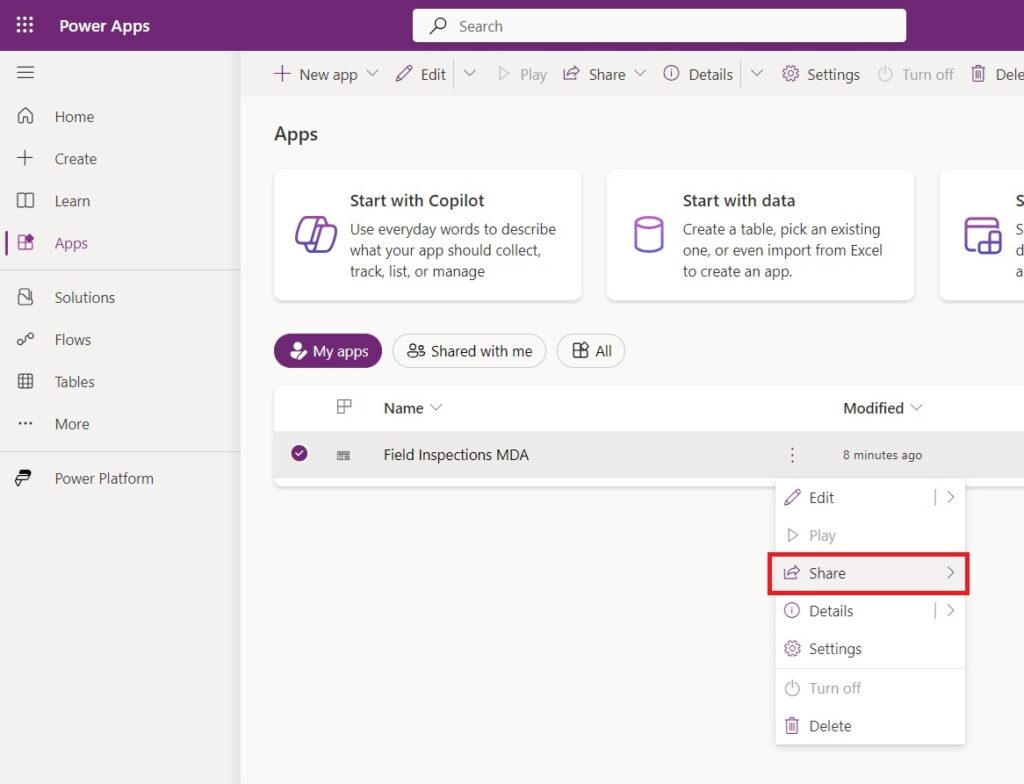
The final step is to share the Field Inspections model-driven app with a security role. Go to make.powerapps.com, locate the model-driven app and open the share menu.
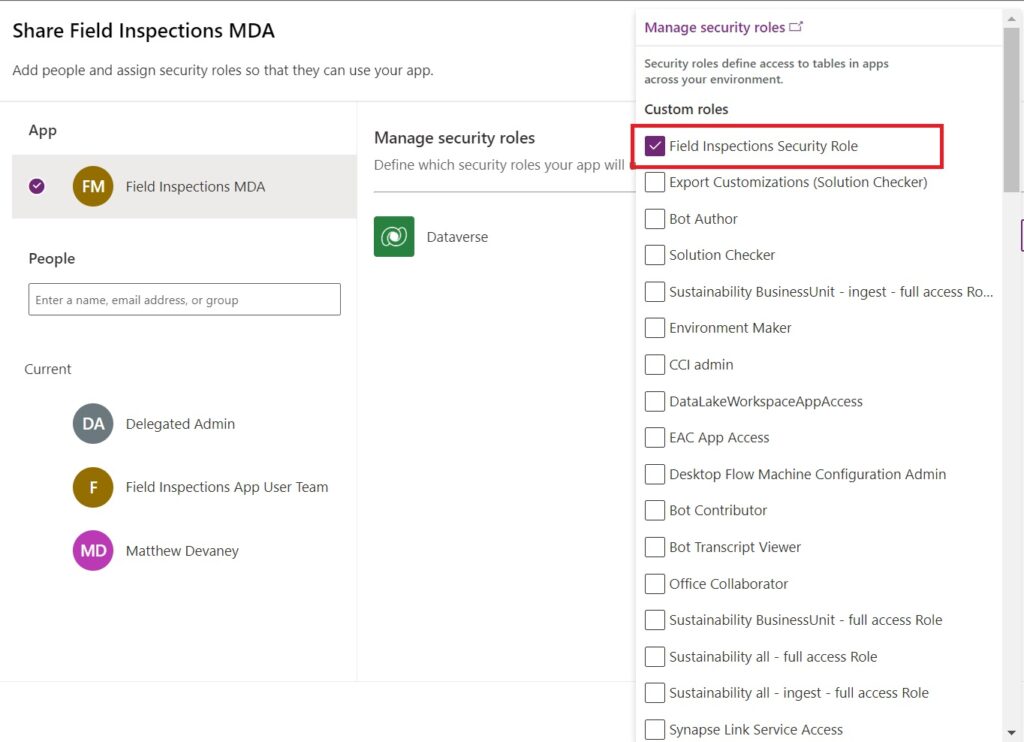
Select the Field Inspections security role. Now any users with the Field Inspections security role will have access to the model-driven app.
Test Access To The Model-Driven App
User has access to the model-driven app, a security and role and the environment simply by adding them to a single Entra security group. Ask a user to open the model-driven app and test their access.
The moment they open the app for the first time they will also appear in the security team.
Did You Enjoy This Article? 😺
Subscribe to get new Power Apps & Power Automate articles sent to your inbox each week for FREE
Questions?
If you have any questions or feedback about Share A Model-Driven App With An Entra Security Group please leave a message in the comments section below. You can post using your email address and are not required to create an account to join the discussion.





Matthew, great post.
I did want to provide my real life feedback on this process though. I have found that once the Entra Security Group has been created it can be assigned directly to a model driven app without a Team already created. When I do this, a team with the same name as the Entra Security Group is created. I do have to adjust Owning Business Unit, Owner of the team and assign the desired security roles, but it removes one step from your process of creating a team.
When I created a team (as you did in your blog), I also found it confusing to see the Entra Security Group Team and the team I had created sitting next to each other.
A need to know for every maker!
Also something te be aware of; as pointed out above, users are added to the environment (and inherent the security roles of the team) the first time they open the app.
That means that on that first run users may lack some privileges, what can result in bad UX.
Of course, it depends on the app scenario.
I recently had a case with an app that fetches data with a flow on opening of the app. But the flow didn’t trigger for new users since they had not yet Read permissions on Process on that moment.
Mehhh 😒
‘Solved’ it with a friendly notification for that first run for new users that some background settings were set and a reload of the app (in-app button) is needed to complete it. All next runs for that user go as they should.
Can we do the same with Canvas Apps based on Dataverse?
Dustin,
Yes, you can.
In your section “Share The Model-Driven App With A Security Role”, I found that even though I’d applied the Security Role to my team previously, in the Environment Settings.
To give the same team permissions when sharing the Model Driven App, just allowing that Security Role access to the app wasn’t enough, I had to then select the same team and give it the same Security role.
I am just wondering why I am having to do this twice but you only had to do it once?
Will users automatically get added to the environment (enabled user) without having to attempt a login?
Currently trying to automate adding new users to an environment that won’t need to actually use the environment/applications in it. They just need to be selectable in user lookup views.
Hello Geremy,
I have exactly this use case. I have 50K+ users in the organization that I may need to do a lookup to but only dozens of users who should actually use the app.
Did you solve this?
Thank you for the great post, I have found this to be a very confusing process.
Replying to Geremy’s comment
G: Currently trying to automate adding new users to an environment that won’t need to actually use the environment/applications in it. They just need to be selectable in user lookup views.
OW: There are two fields that you can use for “User” lookup.
I had started down the path of using SystemUser for my lookups but I am in an org with 70K+ users. By using AADUser you can do a user lookup to the AADUser, if you are using Power Automate you can access user details by using the Entra ID function getUser to get info like email.
There is now no need to add all 70K+ SystemUsers. I am only adding the 20 or 30 SystemUsers that I want to license and assign a security role to.
So my record owners are SystemUsers and all my lookups are AADUsers